Author: Bluetooth Asia Pacific Technical Project Manager either Kay
"Bluetooth Pairing Part 1: Pairing Feature Exchange" talks about the Bluetooth pairing feature exchange of Low Energy (LE). The pairing feature exchange enables both the initiating device and the responding device of the connection to learn the pairing characteristics of each other.
The pairing features that can be enabled are:
· OOB (Out-of-Band) data flag
· MITM (Man-in-the-Middle) flag
· SC- low-power secure connection (LE Secure ConnecTIon) flag
· IO Cap-IO function
After the feature exchange is completed, both devices can select the key generation method used in the next stage. The list below is the conventional low-power pair (Legacy Pairing) and low power secure connection (LE Secure ConnecTIon) of key generation.
Low power traditional pairing:
· Direct connection (Just Works)
· Passkey Entry
· Out-of-Band (OOB)
In addition to the above three methods, a low-power secure connection adds a new method:
· Numeric Comparison
Operational process ( Workflow )
The following describes the key generation operation process of the selected device:
Step 1: Check the secure connection bits in the pairing feature exchange framework. If both secure connection bits are equal to 1, then a low-power secure connection is used and step 2 is entered. Otherwise use low power traditional pairing and go to step 3.
Step 2: When using a low-power secure connection, the initiating device and the responding device should follow the matrix selection pairing method as follows:
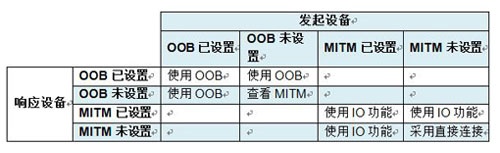
· "Use OOB" means to choose Out-of-Band
· "Viewing MITM" means ignoring "OOB" and viewing the MITM logo
· "Using IO function", go to step 4, select the key generation method according to the IO function of both devices
Step 3: When using Low-Power Legacy Pairing, the initiating device and the responding device should follow the matrix selection pairing method as follows:
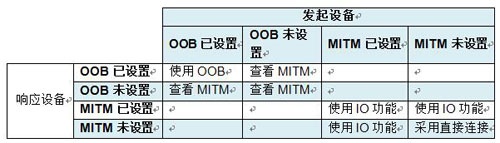
· "Use OOB" means to choose Out-of-Band
· "Viewing MITM" means ignoring "OOB" and viewing the MITM logo
· "Using IO function", go to step 4, select the key generation method according to the IO function of both devices
Step 4: The following is a mapping of IO functions and key generation methods. According to the chart below, both the initiating device and the responding device can find a suitable connection method based on their pairing characteristics.
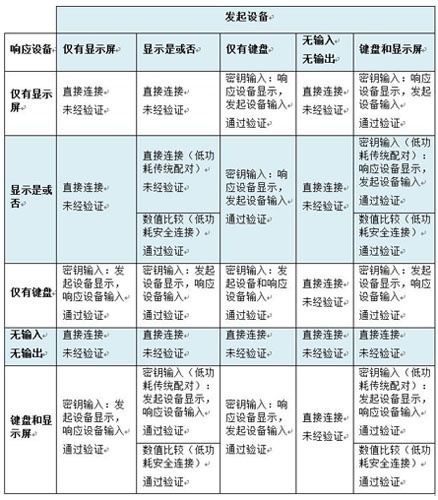
The initiating device and the responding device can then learn how the key generation phase will be applied. A follow-up third article will continue to show how to generate a matching key in a low-power legacy pairing by using Keykey Entry.
About Bluetooth® Bluetooth Wireless Technology
Bluetooth is a universal wireless standard that brings us simple, secure connections. The Bluetooth Technology Alliance teamed up with 30,000 member companies to build a global Bluetooth community. Bluetooth technology creates a unified and harmonious wireless connection between the wide range of interconnected devices around us and powers innovation. With collective intelligence and shared technology standards, Bluetooth brings a simpler, safer and more fulfilling technology experience to users around the world. For more details, please visit.
Transmission poles are tall structures used to support overhead power lines that carry electricity from power plants to homes, businesses and other buildings. These poles are typically made of wood, steel, or concrete and are spaced along transmission lines to provide support and maintain proper tension on the wires. Transmission poles are designed to withstand all weather conditions and are an important part of the grid infrastructure.
Transmission Pole,Steel Power Pole,Steel Fence Posts,Telephone Pole
JIANGSU HONGGUANG STEEL POLE CO., LTD. , https://www.hgsteelpoles.com