Radio Frequency Identification (RFID) technology is a fast, real-time and accurate information acquisition and processing technology. It can uniquely identify physical objects through RF signals, and can be widely used in production, retail, logistics, transportation, medical, defense, Livestock, mining and other industries.
A basic RFID system typically consists of three parts: a tag, a reader, and application support software. Middleware is an important part of application support software. It is a bridge between hardware devices such as tags, readers and enterprise applications such as enterprise resource planning (ERP) and customer relationship management (CRM). The main task of the middleware is to filter, summarize, calculate, and group the data related to the tags sent by the reader, reduce the large amount of original data transmitted from the reader to the enterprise application, and generate event data with semantic interpretation. It can be said that the middleware is the "nerve center" of the RFID system.
For the design of RFID middleware, there are many problems to be considered, such as how to realize many quality attributes of software, how to realize the isolation of middleware and hardware equipment, how to deal with the relationship between equipment management functions, how to achieve high performance data processing, etc. Wait.
1. RFID network framework structureThe frame structure of the radio frequency identification network is shown in Figure 1.
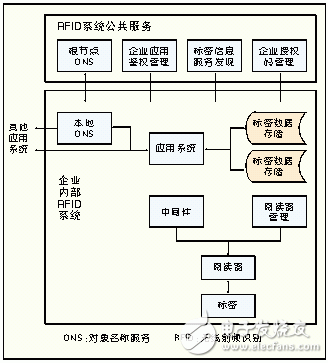
Figure 1: Architecture diagram of the RFID network structure.
The tag data is reported to the application system through packet processing and filtering of the middleware; the application system is responsible for persistent storage of event data, and management of tag-bound business information.
The RFID system shared public service platform provides public services such as root node object name service (ONS), enterprise application authentication management, tag information discovery, and enterprise authorization code management. The root node ONS, together with the internal ONS of all enterprise-level RFID systems, constitutes an ONS tree, and any tag can find the address of the tag information base corresponding to the tag on the ONS tree, that is, the detailed information corresponding to the tag can be further accessed. .
2, middleware function and implementation principleIn a nutshell, the function of the middleware is to accept the request of the application system, and initiate operation commands for the specified one or more readers, such as label inventory, label identification data writing, label user data area reading and writing, label data locking, The tag is killed, etc., and the result data is received, processed, and reported to the background application system.
Among them, label inventory is the most basic and most widely used function.
2.1 Overview of Label Inventory Function
The workflow for tag inventory can be described simply as:
The application system defines the requirements for tag data in the form of rules, which are proposed by the application system to the middleware and maintained by the middleware. The rules define: which readers need to count data, the start and end conditions of the tag data reporting period (event cycle), how to filter the tag data, how to group the tag data, report the data as the original inventory data, add tag data or new Decrease label data, which raw data is included in the tag data, and so on.
The application system specifies a rule to make a reservation for the tag data to the middleware.
The middleware starts the event cycle in a timely manner according to the subscription condition of the application system to the tag data, and issues a label inventory command to the reader.
The reader sends the data counted in a certain period of time (read cycle) to the middleware. The read cycle can be determined by private negotiation between the middleware and the reader.
The middleware is connected to the data reported by the reader.
The middleware performs filtering, grouping, and accumulating operations on the received data according to the definition of the rule, and generates a data result report according to the requirements of the rule at the end of the event period, and sends the data result report to the subscriber of the rule. The filtering process removes duplicate data and data that is not of interest to the application system, greatly reducing the amount of data transferred between components.
See Figure 2 for this process.
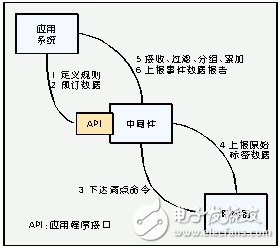
Figure 2: Flow chart of the middleware label inventory summary.
Here, you need to explain the concept of a logical reader.
The middleware abstracts the event source into a logical concept—a logical reader. A logical reader can contain multiple physical readers, and can even be more refined into multiple antennas containing multiple physical readers.
The division of the logical reader can be determined according to the actual system deployment situation. For example, four readers are deployed in two outlets of a certain warehouse, and the four readers can be configured as a logical reader as needed, which may be named as “ Warehouse exit." When the application system needs the tag data of the warehouse exit, the logic reader can issue an inventory command based on the logical reader name as a parameter of a partial application program interface (API) call.
2.2 Label inventory implementation principle
As mentioned earlier, rules are a key element of the overall middleware functionality. The rules are equivalent to the order form issued by the application system to the middleware, which defines the time (event cycle) and specifications (how to filter, how to group, report style, etc.) of the goods (tag data). The principle description part refers to the EPCglobal related content. .
Rules and reports have their own information model, which characterizes the information they carry. At the same time, rules have their own state machine model. These subscriptions trigger a state transition of the rule, such as a transition from an "unsolicited" state to a "requested" state, when accepting long-term subscriptions, single bookings for the application.
Rules are defined by the application system through the API.
(1) Rule information model
The description of the rule information model uses the Unified Modeling Language (UML), as shown in Figure 3.

image 3
In an object-oriented context, rules can be characterized as a class (ECSpec). As can be seen from the description of the information model, a rule class has associations with other classes, or has the following attributes: one or more logical readers (readers), event cycle boundary definitions (boundaries), one Or the definition of multiple reports (reportSpecs), whether the report itself contains the tag (includeSpecInReports).
(2) Report information model
Similar to the rule information model, the report information model is shown in Figure 4.
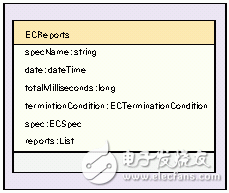
Figure 4: Report information model diagram.
Among them, the event report group class (ECReports) has the following attributes: rule name (specName), time report time (date), event cycle duration (totalMilliseconds), event cycle end condition (terminaTIonCondiTIon), rule definition class instance (spec), one Or a list of instances of multiple report classes (reports).
Specific tag data information is included in the report class (ECReport).
Sync and charge up to 30 tablets, phones, or other mobile device, without the need to connect to a computer
* Provides up to 5V, 2..1A (10Watts) of power per port, for charging battery-intensive devices such as an iPad
* Sync your devices using their file management software, such as Apple iTunes or Apple Configurator, supports USB 3.0 data transfer rates up to 5Gbps;
* Constructed of heavy-duty, steel housing. Build-in 5V 60A power supply with UL certification to keep the safe charges.
* Compatible with any USB powered mobile device,including iPads, Android tablets and e-book readers. Allows simultaneous synchronisation of all devices whilst connected.
* iTunes and Apple configurator enables you to sync your apps, media and usable content from your office, home or classroom. Our Intelligent charging allows you to charge multiple types of devices at the same time whilst ensuring connection stops automatically for each device once fully charged.
30 Port USB 3.0 300W, USB 3.0 Hub 30 Ports with 300W Power,30 Ports Industrial USB Hub,USB 3.0 HUB 30 Ports
shenzhen ns-idae technology co.,ltd , https://www.szbestchargers.com