Orange peel, longan meat, napkins... The “earth method†of unlocking the fingerprint verification of smart phones disclosed on the Internet recently makes the security of fingerprint verification once again affect the nerves of consumers and regulatory authorities.
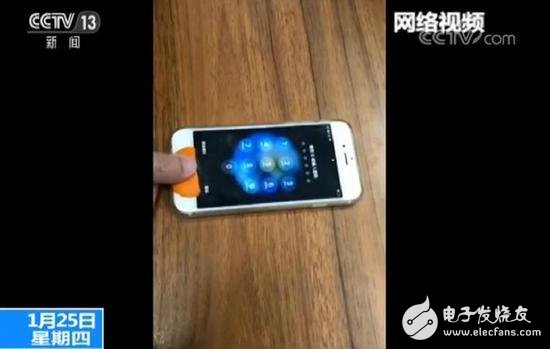
According to the technician, this safety issue comes from the fingerprint verification sensor. It is ironic enough for fingerprint verification, a technology that would make mobile phones, or devices such as door locks, smarter and safer.
What's more, the intelligent era we are in is bringing us more convenience, and at the same time, many people and many devices are at risk of hacking.
Still speaking from fingerprint verificationBiometric cryptosystems, such as fingerprint verification, are about to become obsolete on smartphones, but fingerprint sensors may still exist for many years before they die out, and this also provides a potential target for hackers.
At the 31st Annual Chaotic Computer Club Annual Conference in Hamburg, Germany, hacker Jan Krissler demonstrated how to copy the fingerprint of the German Defense Minister Ursula von Delane, who used only a few of her hand photos and one A fingerprint recognition software called VeriFinger.
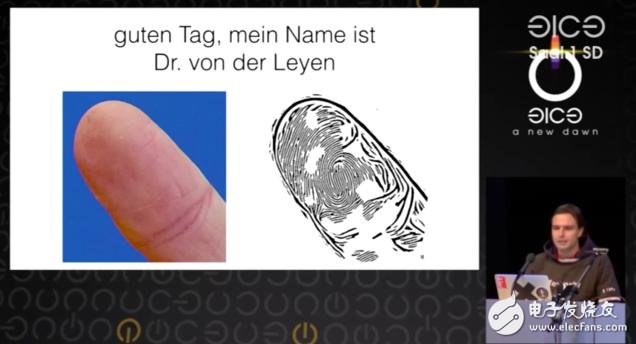
Using a few photos taken from different angles with a standard camera, Krissler copied the complete fingerprint for Ursula von Delaine and made a perfect model that could fool the fingerprint sensor.
In fact, from fingerprint verification sensors, to smart TVs, to 3D printers, to drones, network security research organizations have experimentally verified the possibility of launching an attack.
Just like the title of the movie "Who am I: no absolute security system", there is no absolute security system.
Information security and intelligence go hand in hand, no matter how careful you can't be overemphasized.
Bypass phone sensorResearchers at Nanyang Technological University say your smartphone sensor may reveal your PIN and password.
Using machine learning and information gathered from six different smartphone sensors, they can unlock Android phones with 99.5% accuracy within three attempts, but only if the PIN is in the 50 most common numbers. . Even if it is expanded to 10,000 PIN numbers, the success rate can be maintained at around 83%.
Intrusion of different smartphone sensors often reveals information that the user does not feel quickly. For example, by using a backlight sensor, it is possible to distinguish which button is being pressed according to how much light is blocked.
When smart TV becomes an attack carrierThe average person does not use the TV directly as a computer, but the smart TV does provide a potential target for hackers.
Recently, Rafael Scheel, a security consultant from Oneconsult AG, demonstrated how hackers can gain control without being close to a smart TV: by using a cheap transmitter to embed malicious instructions into a hijacked TV signal, Scheel can signal Get permission for the TV nearby.
Once the TV is compromised, it may be exploited to further attack other devices that are connected to the home at home, or simply use a television camera and microphone to monitor the family members' every move.
Hacking activities in the era of 3D printingAt first glance, it may be difficult to understand why someone would want to invade a 3D printer, not a smartphone. However, when you consider the application of 3D printing in areas such as prototyping, the reason is obvious.
In a 3D printer intrusion demo, researchers showed us how a secret 3D printing design was lost: a team of computer scientists used a built-in sensor from a smartphone to measure the electromagnetic energy emitted by a 3D printer. And sound waves. This allows them to collect enough data and replicate 3D printed objects with up to 94% accuracy.
What is even more worrying is that another group of researchers obtained the permissions of the computer connected to the 3D printer through a phishing attack and modified the 3D model files. The result was a passive failure of a 3D printed drone propeller and the crash of the drone.
UAV-based "flying" hackerWith drone equipment, the risk of close-range "airborne" attacks is rising. In this way, hackers can gain control of other nearby devices.
In order to study close-range attacks on local devices such as set-top boxes, smart watches, and smart refrigerators, researchers from the famous security company Bishop Fox have developed a drone hacker station called Danger Drone.
By using its ability to hover and fly, Danger Drone can be used to carry out attacks on multiple devices in a nearby family.
Acoustic control deviceWhether it's your smartphone or your connected car, hackers may use sound waves to gain access to them.
Researchers at the University of Michigan demonstrated accelerators that trigger microelectromechanical systems (MEMS) through sound waves, that is, chips that indicate whether a device is operating or invade a variety of different devices.
They use a $5 speaker to play sounds of different frequencies, enabling the attacked device to perform various tasks, such as playing a video, opening an application, or even starting a car. Although this type of attack is limited to short-range applications, it is really disturbing to think of using a single speaker to invade a device.
Human beings are the biggest security hole

Overall, the evolutionary history of the Internet is also a history of struggle with hackers, and it is also a continuous network attack and defense war.
For ordinary people, establishing a good sense of security and behavior is the best response. After all, a line in the movie "Who am I: There is no absolute security system": "Human is the biggest security hole."
Din41612 Eurocard Connector Section
Din41612 Eurocard connector Section
Din41612 Eurocard connector Section
ATKCONN ELECTRONICS CO., LTD , https://www.atkconn.com