Author: e Farnell solution development, global director Cliff Ortmeyer
Although the Internet of Things (IoT) is a hot word of marketing, most engineers have long realized that adding connectivity to any electronic device can bring many important advantages. Therefore, the Internet of Things is a very broad term that covers a wide range of applications, from CCTV to IP-connected security cameras, as well as connection sensors for factories and wearable trackers, and even remotely controlled home heating systems.
One of the challenges faced by developers of all Internet-connected devices is security. Mobile payment is an obvious case: banks obviously want to avoid fraudulent transactions in mobile payments. However, IoT security threats come in a variety of ways and have far-reaching implications.
Why is security so important to the Internet of Things? Since the amount of available data is unprecedented, the interconnection and interconnection of all IoT systems and their potential threats have greatly aroused risk awareness. One of the factors that should not be overlooked is that some systems previously developed by engineers did not have access to the Internet, but now they must develop networking products. We believe that banks have strong expertise to ensure the security of financial transactions, but if engineers once only developed a USB webcam, how can we trust him to ensure the security of IP-connected cameras?
Fortunately, if engineers spend some time following some basic guidelines, suppliers, including semiconductor companies and distributors, are now providing technology and support to help develop more secure IoT products.
Risks and threatsAt a recent meeting in Chicago, NXP's Roman Budek said that IoT designers need to consider and address six major security risks. For cloud data and system control, you must consider remote attacks against cloud service providers, and you can't simply think that a major service provider can solve this threat.
The nature of the Internet of Things means that devices are often accessible, and physical attacks on peripheral systems (such as using side channels to control access) are risky for many systems. Similarly, a vulnerable, forged or damaged device can compromise the security of the internal network. And many IoT vendors believe that interoperability with other company products is critical to business success, so this issue is even more of a challenge.
Gateways or IP edge nodes provide an opportunity for remote attacks. In the case of smart homes, gateways are usually low-cost routers provided by customer ISPs, which have limited functionality and may even have unrepaired vulnerabilities.
Smartphones, tablets, and smart watches also have security risks. Users may download rogue software to give them access to the network. Similarly, PIN code phishing software allows devices with applications to gain access to IoT systems. In the end, as the development of the Internet of Things becomes more mature, various devices are upgraded, and the eliminated devices may be implanted into Trojan horses, posing threats to other network devices.
Obviously, when designing an IoT device, engineers need to have a complete understanding of the entire system, rather than just focusing on the product being designed.
Ensuring the security of embedded devicesWhen developing embedded IoT devices, engineers must ensure that the following three things are achieved:
Data integrity: Ensure that data is not snooped, accessible only to authorized personnel, and that data cannot be tampered with to cause deliberate attacks or accidental errors.
Code integrity: Protecting your code is also critical. Code modifications must be detectable and the code can only be modified if authorized. In addition, many companies are also concerned about intellectual property protection issues, which require measures to avoid code theft.
Equipment integrity: Ensure that the connected equipment is reliable and its key functions cannot be tampered with. Therefore, IoT devices require strong encryption key authentication and protection to prevent hacking and product counterfeiting.
To achieve their goals, security experts often refer to the six principles of embedded IoT security to enhance support for developers: identity/authentication, authorization, auditing, confidentiality, integrity, and availability, and the core of many of these principles It is cryptography.
Provide device support for IoT securityThis is good news for IoT product developers, and many devices have provided support for easier build security. For example, the NXP iMX 7Solo application processor, developed in collaboration with the NXP WaRP7 IoT and the wearable development platform, contains many of the built-in security features of the processor.
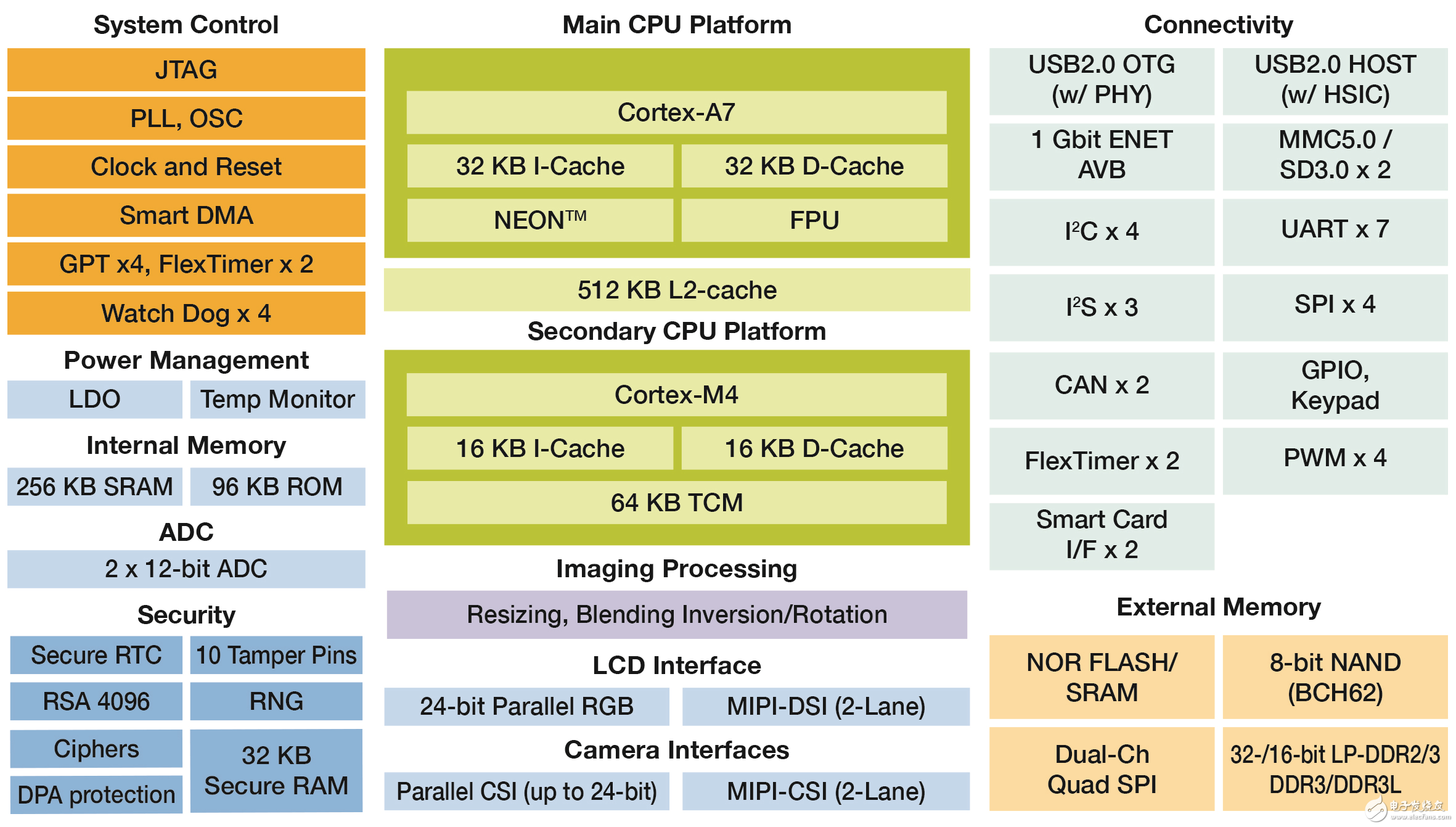
Figure 1 - iMX 7 Solo Application Processor Icon
One of the most obvious features is support for encryption, and the processor also supports hardware accelerated encryption using CAAM (Cryptographic Acceleration and Assurance Module). The module also includes encryption and hash engines that support various encryption standards.
There are two basic types of encryption algorithms: symmetric and asymmetric, and choosing the right algorithm is critical to IoT system design. Symmetric algorithms use the same key to encrypt and decrypt data with less processing overhead.
Asymmetric encryption uses a "one-way" approach with a pair of keys. The private key is kept secret and is not distributed to the public, while the public key is shared publicly. If you use public key encryption, you need to use the private key to decrypt, and vice versa. This method makes the system easier to manage and more scalable.
The Random Number Generator (RNG) is one of the requirements of the encryption algorithm. This can be used to generate keys, which must be randomly generated to prevent hackers from predicting keys and cracking passwords.
IoT devices can be developed by providing on-chip hardware support. Not only does this use strong encryption to ensure a higher level of security, it also does not have a significant impact on the processor running the application.
The processor used on the WaRP7 board also uses a simple SPA or Differential Power Analysis (DPA) to prevent predictive keys.
IoT security can also be enhanced with other features, such as processors and other processors used on WaRP7.
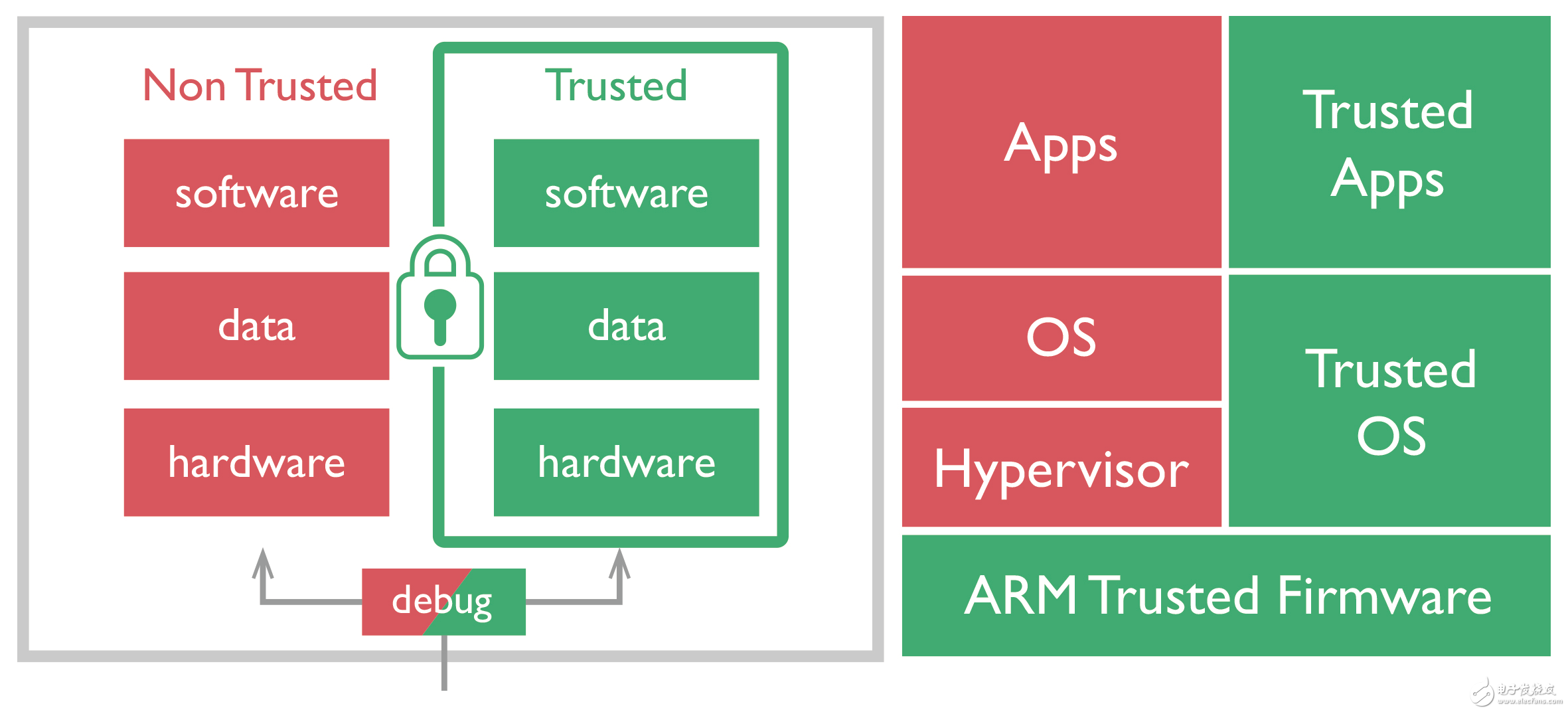
Figure 2 - ARM Trust Zone
Processing complexityThis article uses only some features of an IoT board to enhance security as an example. The challenges faced by engineers are the complexities presented in this article. Obviously, engineers need support to make sure they have time to learn these features.
First, choosing the right development platform is critical. Many resources, such as the design center of the e-Community community, provide detailed information about processor development platforms, software tools, and middleware. Application engineers and distributors such as the e-Community play an important role in ensuring the production of the right components, while also reducing the learning curve for selecting the right tools and information.
The current highly integrated state means that the development platform usually has only a few components, which is almost the ideal hardware for production. We cooperate with many companies to create existing development boards such as Raspberry Pi to meet their specific needs, or to develop hardware according to specific requirements, so that more engineering resources can be applied to most complex and product differences. In larger code.
Conclusion - Security issues are one of the biggest challenges for the Internet of ThingsToday, almost all electronic devices benefit from network connectivity, whether it's remote control, monitoring, or simple logging or data analysis. However, network connectivity poses many potential risks and must be addressed with appropriate device and system level security tools. As semiconductor and software vendors provide secure support from encryption to physical security, there is no excuse for developers of IoT products to evade product security. However, the challenge for engineers is to overcome the inevitable complexity of additional features. Therefore, they must seek help from suppliers like the Internet Alliance to meet the challenge.
VOZOL D5 Vape are so convenient, portable, and small volume, you just need to take them
out of your pocket and take a puff, feel the cloud of smoke, and the fragrance of fruit surrounding you. It's so great.
We are China leading manufacturer and supplier of Disposable Vapes puff bars, vozol d5 disposable vape,vozol d5 vape kit,
vozol d5 vape pen, and e-cigarette kit, and we specialize in disposable vapes, e-cigarette vape pens, e-cigarette kits, etc.
vozol d5 disposable vape,vozol d5 vape kit,vozol d5 vape pen,vozol d5 vape 1000 puffs,vozol d5 e-cigarette 1000 puffs
Ningbo Autrends International Trade Co.,Ltd. , https://www.supervapebar.com