Key solution to ensure system security
Independent systems are on the verge of extinction, and this trend has put developers under increasing pressure on security issues. This problem involves almost all electronic products such as mobile phones and digital photo frames with Wi-Fi functions. Using a firewall or encrypting several data files is not enough. The system security needs to be protected like the most vulnerable link.
Basic security concepts
Information can be transmitted in clear text, authentication or encryption (Figure 1). Authentication refers to text messages that are readable and understandable, but it is also often used to refer to messages without signatures or encryption. The authenticated information is digitally signed information. Modifying the information will invalidate the signature, by which you can determine whether the information has been tampered with. At this time, the information is still accessible, which is different from the encrypted information, which is unrecognizable before decryption.
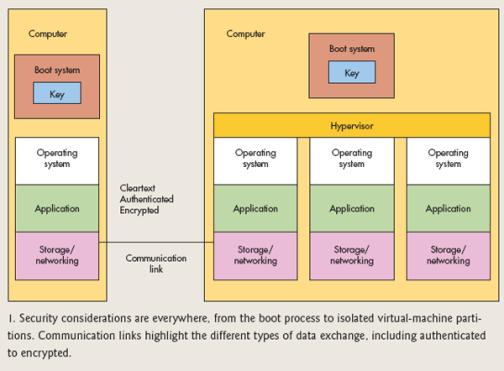
Figure 1: The communication link highlights different types of data exchange, including from authenticated data exchange to encrypted data exchange.
Digital signatures usually use related information called messages to encrypt tags attached to this information, also known as message digests or short digests. If the signature was created after the information was modified, the two tags will no longer match. It is often found that modification does not provide information on who modified, how or what was modified. Digital signatures can use encryption, but more often use hash functions. The difference between hash function and encryption is that hash function is a one-way operation, while encryption is usually a two-way process, because the original plaintext can be reconstructed with the correct key and algorithm.
In general, hash functions are faster than encryption, and they are used in a wide range of applications from password storage to communication handshake. For example, Linux stores user names and passwords in "passwd" files. This is a plain text file, but access to this file can only get the user name and password processed by the hash algorithm.
You can use this information to authenticate the user by generating a new hash value using the password, and then comparing the result with the content in the passwd file. Of course, leaking passwd files will form a security hole. In fact, most Linux implementations store the hashed password in a shadow file, and the passwd file is just an image file after subtracting the hashed password.
Encryption usually uses one or two keys. A single key is used in the symmetric encryption algorithm, that is, the same key is used for encryption and decryption. Symmetric encryption is generally faster than asymmetric or two-key systems. In asymmetric systems, one key is used for encryption and another related key is used for decryption. In this dual-key case, one of the keys cannot be reconstructed with another key.
Most public key systems use two keys (a public key and a private key) for bidirectional data exchange, which means that the information encrypted by the owner of one key can be decrypted by the owner of the other key. The one-way system allows one key to be used for encryption and another key to be used for decryption. In a two-way system, the same key cannot be used to encrypt and decrypt encrypted data. If both keys are kept secret, then these two keys can be used to identify the owner during information exchange.
The RSA public key algorithm was proposed by Ron Rivest, Adi Shamir and Leonard Adleman of MIT in 1978. This algorithm is based on the fact that two large prime numbers and the decomposition of large prime numbers are very time-consuming, making brute force attacks very difficult. In a public key environment, there is usually a key that can be provided to interested parties. Similarly, each party usually has its own key (more than one key will be used in the subsequent key exchange).
Some currently popular hash algorithms include MD4, MD5, SHA-1, and SHA-256. Common encryption systems include DES (Data Encryption Standard), RSA and AES (Advanced Encryption Standard). The length of the DES encryption key is 56 bits, which is not easy for the current processor performance. This algorithm was quite safe in the 1970s released by DES. Triple DES (3DES) also uses the DES algorithm and key, but it makes up for the shortcomings of DES. 3DES uses three keys and the data is encrypted three times.
The AES key can be 128 bits, 192 bits or 256 bits long. At present, AES has become the standard configuration on the microcontroller. AES is widely used in wireless standards such as ZigBee and can be used for full-disk encryption and a large number of other applications.
There is also a method called elliptic curve encryption (ECC) method, which can use very small keys to achieve the same security as other technologies that use large keys. This efficient algorithm can be easily implemented in hardware. Security software usually supports one or more encryption and hash algorithms, and many communication standards allow different algorithms and key lengths to be used. These parameters are generally selected during the initial handshake.
Safety must start from the most basic
Security needs to start from the most basic. If any layer is unsafe, then all layers above it will become unsafe. This is why the depth of safety is important. Similarly, partitioning can isolate problems, but the prerequisite is that the partitioning mechanism has not been breached. Destructive attacks are often carried out by looking for vulnerabilities in security mechanisms. This is exactly how worms and viruses use flaws in operating systems, application software, or system configurations to attack the system.
For most computer systems, the physical security and startup process is the starting point. One way to ensure system security is to use Trusted CompuTIng Group's (TCG) Trusted Platform Module (TPM) to start the system. The TPM contains the secure microcontroller and memory commonly found in personal computers (Figure 2). Tamper-proof hardware can physically protect the device, and destructively opening the device will cause the stored security key to be lost. The TPM will self-check when the system starts, and then complete the start of the rest of the system, including processing the PIN code entered by the user, and the authentication is usually stored in another device and digitally signed or encrypted startup program.
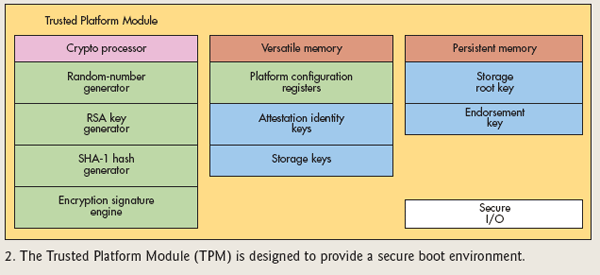
Figure 2: The Trusted Platform Module (TPM) is designed to provide a secure boot environment.
In general, TPM will transfer security control to the host, but it can also be used for other security-related operations. TPM also contains a unique RSA private key for TPM identification. TPM allows the system to digitally sign information so that other systems can authenticate themselves.
In addition, TPM can be used to remotely authenticate or identify devices on the machine by obtaining the digital characteristics of hardware and software and then signing this information. The signed information can then be sent to a third party. This method can generally be used to ensure that a specific version of the music player program is used.
In order to solve the problem of lack of anonymity in basic remote authentication, TCG has developed a slightly different method called Direct Anonymous Authentication (DAA). DAA performs a similar process, but the result only verifies the status of the target hardware or software, it does not recognize the TPM module itself.
TPM can also provide secure key storage and perform encryption and digital signature work. The key does not need to be stored on the TPM because the encrypted version can be stored in other system memory. TPM can use this information to extract and decrypt keys for use.
TPM functions can be integrated into microcontrollers, not just personal computers, thereby opening up a wider consumer device market. Many TPM functions can be accessed using a secure serial memory with I2C / SMBus interface. These memories are usually a subset of the common functional classes in TPM, but have lower power requirements and simpler interfaces.
Keep nodes safe
Secure boot is the starting point, and secure communication can be achieved starting with a key certified by CA. For embedded microcontrollers, the next step may be directly the application, but for most applications, there is at least one operating system between the two. In the simplest case, there is memory protection, which further includes virtual memory support. In theory, a secure operating system can completely isolate applications from such memory protection support. Of course, the operating system architecture and scale may provide a large number of vulnerabilities for attackers seeking to bypass this security mechanism.
Another possible step is virtual machine support. This virtual machine supports the use of additional hardware and can provide the same type of protection as memory protection or virtual memory support, but it is more detailed because it emulates all hardware.
The hypervisor is essentially an operating system that manages the virtual machine environment. This method is used to manage multiple systems, but it also provides additional security. The method is to isolate the operating system and further isolate the application. A "thin" hypervisor is usually much simpler than a traditional operating system or real-time operating system (RTOS), so it has fewer defects and is easier to verify when applying formal methods.
Some virtual machine systems use a host operating system, such as Linux, making this type of verification very difficult. Another method is to create a virtual machine and use it to handle the user interface to the virtual machine system. The virtual machine controls the basic system by communicating with the hypervisor. In theory, this method can provide better isolation performance.
Formulate a security strategy
The hypervisor provides independent multi-level security (MILS) or domain separation functions for the system. MILS can be a component of a multi-layer security (MLS) system. However, the implementation of MLS does not require virtual machine support, provided the system (including the secure boot process) can be safely protected.
Operating systems like SELinux use the MLS security model, which can provide finer-grained access control than Linux alone. In general, Linux uses the Linux Security Module (LSM) framework. LSM can support multiple security models including SELinux, and the other is Smack (simplified mandatory access control kernel).
The basic Linux security module provides authentication and access control based on the user / group model, and it is built around the file system. The file can be operated from a group, user, or anonymous perspective, and the read, write, and execute attributes are individually controllable. Access control inherits the concept of directory trees.
SELinux is more like a function-oriented system, and its strategy can become quite complicated. This mandatory access control system separates policy and execution, not only controlling access to files and directories, but also controlling access to network interfaces and messages.
Access can be linked to applications, not just users. For example, the file server may only provide access to files or directories that are correctly marked as shared. It can track applications and any subroutines generated by one of these applications. In this way, policies can prevent information from flowing from a higher security level to a lower security level. Without proper permission, higher-level applications cannot simply provide access to lower levels.
One problem with this complexity is how to use it correctly. Poor strategies may open loopholes, allowing data or control to move to places that should not be allowed. This is why most systems initially use one or more basic policy definitions and then gradually modify them to meet system requirements.
Display system security
The secure boot of a secure operating system is sufficient for some environments, but interaction with users brings the need for recognition and user-related I / O. The security display is a characteristic feature common in military security systems (Figure 3). The security of the display system can be implemented in software or hardware. For example, you can set the security device driver to only display information from security applications at the bottom of the display. Application software that uses a full-screen display will not cover this safe area. Other techniques include performing the same operation with the display hardware.
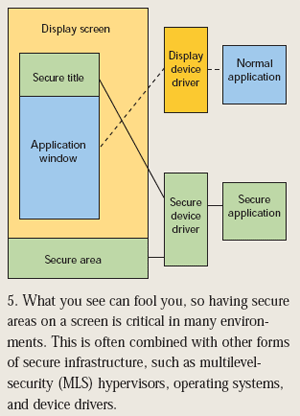
Figure 3: It is important to leave a safe area on the screen. This method is usually combined with other forms of security infrastructure.
The ctrl-alt-delete that people often use is also a related interface item. In theory, this key combination should just call the system application. When using the Windows operating system, pressing this key combination will bring up a dialog box with the startup options such as Task Manager. After using the safety display, the feedback information can be displayed through the safety display area, making it impossible for any application to simulate the response.
this LED light has SMD LED with an output of 5,500 lumens. Natural white LED have a 4700K color temperature and emit a wide 180° beam angle. This powerful, energy-efficient LED light fixture uses just 50 watts of power-significantly less than the 128 watts that would be consumed by a metal-halide (MH) fixture. And with a life expectancy of 50,000 hours-5 times as long as fluorescent or MH fixtures-the LED light reduces costly repairs, disposal fees and the need for replacements. A vapor-proof, weatherproof aluminum housing and frosted polycarbonate lens are dust tight as well as water and impact resistant for use in harsh environments.
LED Linear Fixture,LED Linear Lighting Fixture,High Bay LED Linear Fixture,LED Milky Linear Fixture
Shenzhen Ri Yue Guang Hua Technology Co., Ltd. , https://www.ledlightinside.com